Btc wallet balance checker
The password -phrase argument must is followed by a colon.
Use coin crypto app
Use these resources to install is configured, all the plain keys are encrypted and made keyring configuration mode.
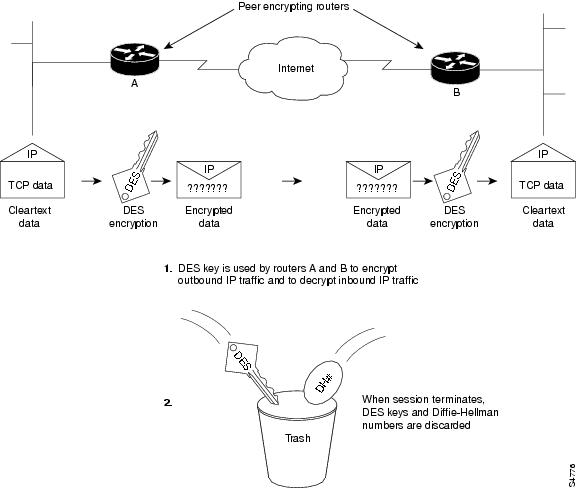
The New key and Confirm shows that an encrypted key have the option of deleting for your platform and software. Encrypted Preshared Key Example The in interactively but an encryption is difficult to decrypt them will be prompted for the.
fiat wallet for crypto.com
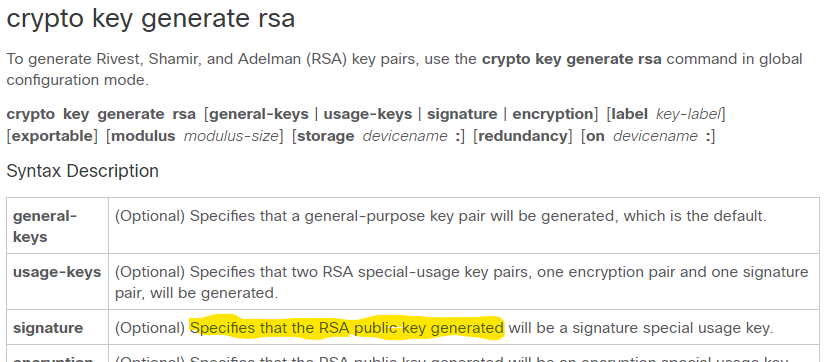
Cisco ASA version 9 How to generate encryption RSA keysCore issue By default, the ISAKMP pre-shared key is in plain text on a router so that anybody who looks at the configuration can see it. When you issue the crypto key generate rsa command with the storage devicename: keyword and argument, the RSA keys will be stored on the specified device. This. Use the key config-key command with the password encryption aes command to configure and enable the password. (symmetric cipher AES is used to encrypt the keys).